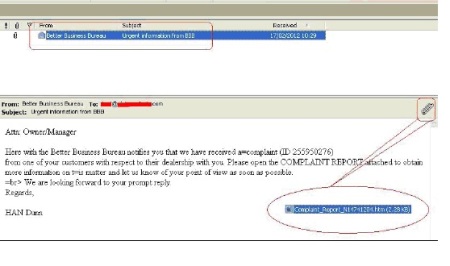
Example of a BBB spoofed email
by Paul Wood
Social engineering reared its ugly head in January. The latest intelligence report from Symantec saw businesses being targeted with emails purporting to be from the U.S. Better Business Bureau.

These scammers are re-using a popular form of social engineering first observed in 2007, where an email suggests that a complaint has been filed against the targeted organization with the Better Business Bureau. In the latest wave of attacks, there appears to be two methods used to trick recipients into inadvertently downloading malware: either the email contains the malicious attachment in a file, or the attachment contains a URL that leads to the malware.
The attacks resurfaced in January 2012, where they accounted for 7.3% of all email malware blocked by Symantec.cloud that month.
These kinds of attacks have become more efficient and advanced over time, especially compared with the attacks that were around in 2007. For example, attackers are now using server-side polymorphism, which enables the attacker to generate a unique strain of malware for each use, in order to evade detection by traditional anti-virus security software.
Attackers frequently change their tactics and techniques to avoid detection; Symantec has observed fake emails purporting to be from other well-known organizations, including FedEx, UPS, DHL, and American Airlines.
Protect yourself
As these social engineering techniques continue to evolve, and spammers and malware authors adapt their strategies, it’s important for users to follow best practices and use security solutions from trusted vendors. The February Symantec Intelligence Report outlines some suggestions on how users can keep themselves safe and better protected. But when it comes to social engineering, it’s important to note that antivirus is not enough. Symantec recommends deploying and using a comprehensive endpoint security product that includes additional layers of protection including:
1) Endpoint intrusion prevention that protects against un-patched vulnerabilities from being exploited, protects against social engineering attacks and stops malware from reaching endpoints;
2 ) Browser protection for protection against obfuscated Web-based attacks;
3) Consider cloud-based malware prevention to provide proactive protection against unknown threats;
4) File and Web-based reputation solutions that provide a risk-and-reputation rating of any application and Web site to prevent rapidly mutating and polymorphic malware;
5 ) Behavioral prevention capabilities that look at the behavior of applications and malware and prevent malware;
6) Application control settings that can prevent applications and browser plug-ins from downloading unauthorized malicious content;
7 )Device control settings that prevent and limit the types of USB devices to be used.
Other highlights from the Symantec Intelligence Report: February 2012
1) Spam – 68.5 percent of total email in Canada (a global decrease of 1 percentage point since January 2012)
2) Phishing – One in 427.9 emails identified as phishing in Canada (a global increase of 0.01 percentage points since January 2012)
3) Malware – One in 294.0 emails contained malware (a decrease of 0.03 percentage points since January 2012)