Rogue antivirus – also known as scareware – is one of the top PC security threats in Canada and proving an effective method for online fraudsters to profit from their exploits, say security experts.
The malware tricks victims into thinking their computer is infected and provides a fake piece of software to fix the problem.
After giving away credit card information and downloading the software, the victim actually is opening up a direct gateway for more malware to be loaded onto the computer and becomes a prime candidate for identity theft. The double-whammy attack is proving effective and becoming more popular among hackers.
Microsoft Corp.’s security products removed scareware programs from 7.8 million computers worldwide during the second half of 2009, an increase of 46.5 per cent from the previous six-month period. That suggests scareware is providing better payoffs to cyber-criminals than other types of malware, according Microsoft Security Intelligence Report Volume 8.
“The biggest threat facing Canadian PCs is fake security software,” says Mohammad Akif, national security and privacy lead with Microsoft Canada Inc. in Missisauga, Ont.
Related story
Hackers exploit Polish president’s death with massive scareware attack
The top two scareware infections were removed nearly 230,000 times in Canada during the second half of 2009. That’s close to double the second place infection rate in the country. It’s a blemish on an otherwise gleaming report card for Canadian PC security.
Only three in every 1,000 PCs are infected in Canada, Microsoft estimates. That’s well below the global average of seven per 1,000 PCs, and an improvement over one and a half years ago when Canada had an infection rate of eight per 1,000 PCs.
Scareware tactics continue to be popular among hackers in 2010, according to Romania-based security software vendor BitDefender. Rogue antivirus malware appeared as the third-highest ranked threat in April, accounting for 2.72 per cent of all PC infections worldwide. The detection is based on javascript code triggered on Web sites that push users to download the malware using fake alerts.
“Most of the time, that’s enough to dupe you into purchasing the product,” says Catalin Cosoi, head of the online threats lab at BitDefender. “It wouldn’t be easy for malware to reach the top five if it wasn’t already there. I guess this was pretty successful.”
Dubbed “Security Center”, the scareware is coded in Delphi and almost 2 MB in size. It asks the user to pay $84 for full software that can remove a fake infection. In addition to the pop-up windows pushing victims to make the purchase, the audio of a lady’s voice is played warning of an infection.
This attack was conducted 3,000 times per day in April on many BitDefender customers, Cosoi says. Those users were protected from the malware.
Ironically, cyber-criminals pushing scareware may be benefitting from increased consumer awareness about the need for antivirus software. Advertising campaigns conducted by legitimate security software vendors have established the general knowledge that Internet threats exist and there are ways to protect a PC.
“If you don’t know the real products, there’s a high chance you’ll end up with a fake one,” Cosoi says. “Both real security companies and fake ones advertise the same thing — that you should have some protection when you use your computer.”
It is common for scareware to emulate legitimate brands, such as Microsoft and McAfee. To the untrained eye, it could be easy to miss the difference.
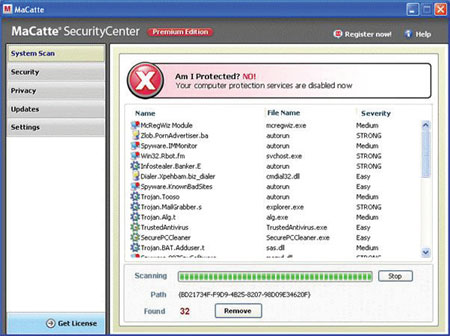
“It’s a matter of trust,” Akif says. “You trust your security [software] the most, so you will basically click yes and bypass all the security checks put in place.”
Scareware hackers are also selective about their targets. They target geographies where people are fairly wealthy and more likely to use credit cards, according to Microsoft’s report. For instance, Norway is one of the countries with the highest per-capita GDPs in the world, and scareware accounts for six out of the top 25 classes of malware. In China, where credit cards are rare, none of the top 25 threats are scareware.
It just reiterates that hackers are out for financial gain now more than ever, Akif says. “They will find something of value and they’ll try to steal it.”
More aggressive ‘ransomware’
Scareware or rogue antivirus software that acts more aggressively in trying to illicit a payment from victims is dubbed “ransomware” by security researchers. BitDefender cites an example, dubbed Security Tool, that comes in a fairly large package, over 1 MB in size.
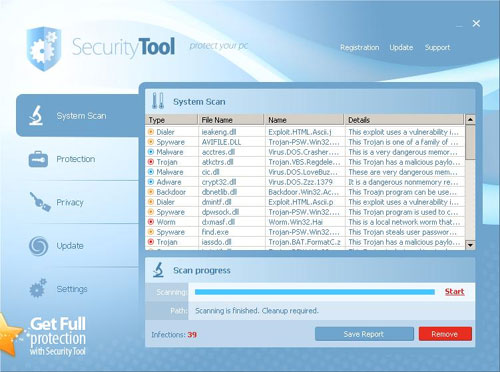
Among other behaviours, the insidious malware createsa desktop shortcut for itself and bombards the user with pop-up notices to buy the “full version..” It then starts to remove other shortcuts from the desktop, close open applications, and trigger firewall alerts when Web browsers are opened.
A screensaver faked the blue screen of death, and any information collected about the infected PC was transmitted to a remote server.
“It’s not just scareware anymore,” Cosoi says. “It’s actually ransomware because it’s very aggressive and won’t let you use the PC.”
Follow Brian Jackson on Twitter and check out the IT Business Facebook Page.




