Mobile devices are being increasingly targeted by hackers looking to scoop financial information they can use to steal money and the trend is only going to get worse as smartphones become payment methods in their own right, according to security vendors.
Hackers are disguising Trojans as legitimate apps, and that malware sometimes gets lost among the tens of thousands of apps available for download from digital storefronts such as Google’s Android Marketplace or Apple’s App Store. Many next-generation smartphones will include a near-field communications (NFC) chip, which is the same contactless technology used by MasterCard’s Paypass or Visa’s payWave system.
Related Story: Protect your Android phone with security apps
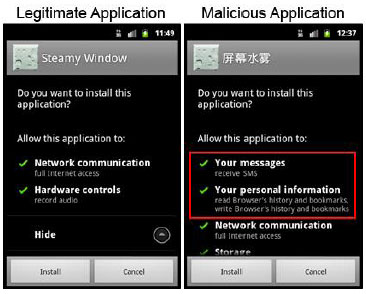
An example of an Android Trojan (right) that mimics a legitimate app (left). Source: Symantec Corp.
Once smartphones store financial data onboard and are used to make transactions, they’ll become more targeted by hackers, according to Symantec Corp. “That’s going to be what triggers it,” says Marc Fossi, the editor of Symantec’s latest Internet Security Threat Report, released today.
“The more users use their smartphones for online banking, the more chance hackers will have to steal their financial information,” he says.
NFC chips primary use will be to link to credit card or bank account information, says Stewart Cawthray, senior security achitect with IBM Global Technology Services. This means that a smartphone suddenly becomes a much more expensive item to lose, as criminals could access those account.
“Service providers who offer the NFC enabled devices should offer a quick way to remote disable the device if it is reported stolen to prevent fraudulent use. Financial intuition’s can also help with policies similar to what they have for stolen credit cards to limit losses to NFC transaction fraud,” Cawthray says. “The single greatest thing a consumer can do to protect themselves is enable a password to unlock the device before the NFC chip will function.”
In 2010, there was a 42 per cent increase in the number of mobile vulnerabilities disclosed – from 115 vulnerabilities in 2009, to 163 last year, according to Symantec.
IBM Corp. also pegs the number of mobile vulnerabilities for 2010 at 163, but shows a much sharper rise from its 2009 count of 70 vulnerabilities. IBM also counts the number of exploits released – malware actually designed to take advantage of mobile vulnerabilities – and counts 14 mobile exploits released in 2010, compared to just two released in 2009.
IBM reported its research in its X-Force 2010 Trend and Risk Report, released March 31.
Many hackers are taking advantage of users who are looking to “jailbreak” or “root” their smartphones in order to gain additional functionality and by-pass application storefronts, IBM says in its report. This drives the creation of reliable exploit code that can be repurposed by hackers for malicious means.
DroidDream was an example of root-access malware that affected Android version 2.2 and earlier phones in March. Google responded to the Trojan by sending out a mass remote kill that wiped it from all devices it had been installed on, and removing it from Android Marketplace. The Trojan collected personal information from the phone such as the SIM card’s International Mobile Subscriber Identity and sent it to a remote service based in Fremont, Calif.
Samsung’s Nexus S smartphone includes an embedded NFC chip. It is being launched in Canada by Telus this sometime Spring. It will run on Google’s Android 2.3 Froyo operating system.
IBM recommends several basic controls to boost security on mobile devices:
- A strong device password.
- A quick lock-out time if the device is inactive.
- A mechanism that wipes device data after enough password failures.
- Install an anti-malware program if the device can access business data or infrastructure.
- Protect the device with firewall controls if possible
- Configure Bluetooth so it is not discoverable and will only connect with paired devices
Gone are the days when mobile malware could be discounted as an “urban legend,” IBM’s report says. Though not as pervasive as PC-based threats, mobile malware shouldn’t be discounted by businesses.
IBM’s Cawthray also offers some advice to SMBs – manage your mobile devices like a laptop computer. Also, educate users on the risks of using mobile devices with sensitive data and how they can protect it. Have a plan in place if a device is lost or stolen.
Hackers sold many terabytes of personal information in the underground online economy and made healthy profits, according to Symantec. Credit cards are the top advertised item being sold by hackers, in bulk packs ranging from 10 cards for $17 to 1000 cards for $300.
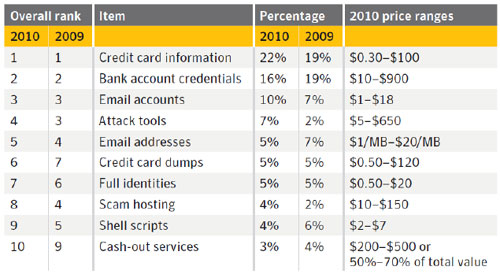
Symantec’s data on advertised rates for personal information sold via the underground economy.
Brian Jackson is a Senior Writer at ITBusiness.ca. Follow him on Twitter, read his blog, and check out the IT Business Facebook Page.




