Nearly 60 per cent of businesses have automated their security and incident response tools, but only at a very minimal level, according to a new SANS Institute study.
The D3 Security sponsored study on automation and integration indicates that while most respondents agree automation isn’t killing jobs in the security field, few have gone past automating the most basic and repetitive tasks. But the low hanging fruit yields quick, measurable results, says Stan Engelbrecht, D3 Security’s director of cyber security practice, and gives skilled staff more time to focus on bigger picture items.
“There’s a lot of manual clicks and copy and pasting that doesn’t need to happen,” he says.
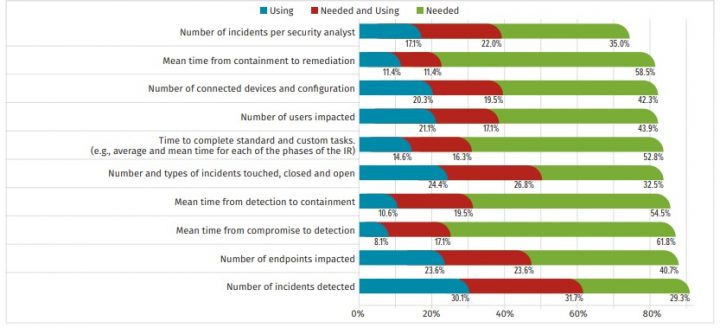
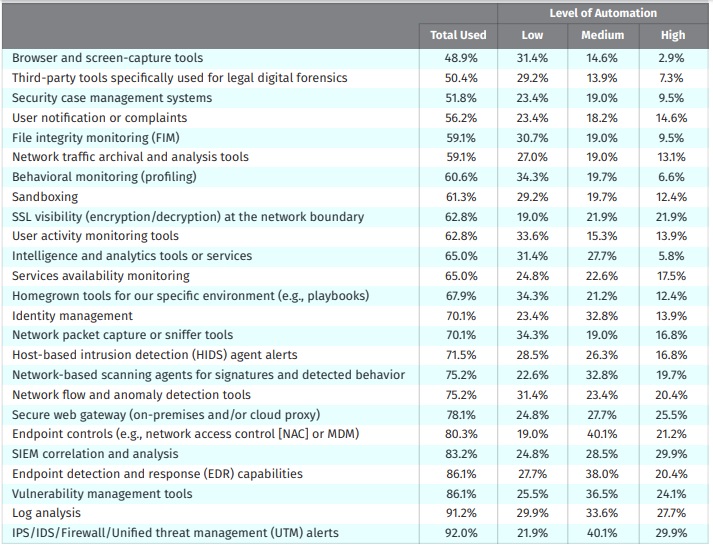
Integration Survey.
But outside of those repetitive tasks, security teams are having a hard time convincing executives to invest in more sophisticated automation that allows for real-time analytics and endpoint device management. Nearly 60 per cent of the 218 technology professionals – 70 per cent of whom described themselves as security pros, the rest are categorized as analysts and upper management – claimed budget restrictions were the number one concern around automation. That was very closely followed by resource constraints and lack of integration standards.
“If you are going to automate, this has to come from the top down. If there isn’t an executive management buy-in, it won’t work,” says Engelbrecht.
In a nutshell, everyone’s level of automation is relatively low, few are innovating at a high level, and most businesses are heading into the middle. No one is using AI and machine learning.
AI not there yet, not even close
“I have not seen good implementation of AI or machine learning, where you’re actually able to prove and show exactly what it’s doing,” says Engelbrecht.
But there shouldn’t be any rush to try and achieve this. In fact, before integrating basic automation, companies should start by creating a playbook, a collection of processes and operating procedures that conform with the policies and culture of an organization, something respondents had trouble doing in their open-ended responses, the study notes.
Fast-tracking automation can actually be dangerous, explains Engelbrecht. The toughest, most malicious cases still need hands-on, critical thinking from a security analyst. If he or she is suddenly cut off from the flow of information, bad habits are sure to form.
More than 57 per cent of respondents anticipate changes to the focus of their use of automation in the next 12 months. Nearly 30 per cent remain unsure. The banking industry has been far more successful at integrating automation, according to Engelbrecht.
“When you walk into a bank and having a lot of those early conversations, that whole process, and knowing what exactly that needs to be automated, is easy,” he notes. “Healthcare is another good example. They’re getting better, but still behind the curve.”





